Large companies face greater CMMC compliance challenges: CMMC for multiple CAGE codes. Mergers and acquisitions create a lag of vertical alignment among IT and shared services. And IT systems aren’t designed to segregate and manage CUI and FCI. We also find that rapid growth complicates management’s ability to track all the touch points as CUI and FCI flow through departments and affiliates.
One SSP for multiple CAGE Codes
Fortune 500 companies typically require CMMC levels 1 and 2, while also being eligible for COTS exemptions. KLC Consulting identifies the efficiency opportunities to create one SSP for multiple CAGE Codes and has depth of experience designing the most complex CMMC compliance programs for large companies.

TL;DR: CMMC for multiple CAGE Codes: Can a company file one SSP in the DoD’s SPRS that covers multiple subsidiary CAGE Codes? The answer depends on the degree of vertical IT integration. “One SSP for All” doesn’t work when mergers & acquisitions fuel growth and vertical IT system integration lags.
KLC Consulting finds compliance efficiency opportunities by inheriting common controls, policies, and procedures.
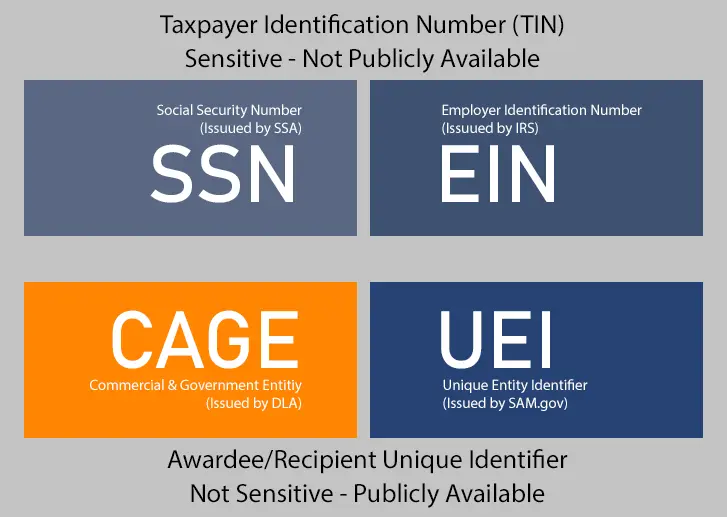
A CAGE Code – Commercial and Government Entity Code – is a five-character alpha-numeric, unique identifier assigned by the Defense Logistics Agency (DLA). Your CAGE code would be the first question a prime contractor asks you if you are a new subcontractor to them. That’s because it is integral in the establishment of security requirements for any project that involves defense contracts, especially secured information, (FCI/CUI/CMMC).
A company must obtain a CAGE Code to do business with the federal government. A CAGE Code is assigned to each separate operation of a company and can be applied to almost any product or service they offer. Since 2014, CAGE codes have been required for federal government contractors to create a uniform, national system for tracking hardware, software, and technical data when transferring such items between DoD contractors and DoD components.
CAGE Code Requirements for Multiple Locations
A company can have one or more CAGE codes. When the DOD contracts with an organization, they identify the organization by its CAGE code. In DFARS 7012, 7020, and CMMC, The DOD expects DIB contractors doing business as prime or sub-contractor to create a System Security Plan (SSP). By registering your CAGE Code, you will be able to win more government contracts and gain valuable new clientele.
What if I have more than one?
The DoD requires you to have an SSP to satisfy the DFARS requirements. This doesn’t necessarily mean you have to create a unique SSP for each CAGE Code. However, you must have an SSP to support each CAGE Code. For instance, if you have 10 CAGE Codes, and they perform very similar functions and are on the same network, you may be able to include them into one information system and create one SSP to cover all 10 CAGE codes. Moreover, If your company has seven CAGE Codes that perform the same function, and three CAGE Codes are under a newly acquired subsidiary, you might satisfy DFARS and CMMC requirements with two SSPs.
Only large companies have more than one CAGE Code?
No, not necessarily. Some companies have a different CAGE Code for each business unit. They believe they can manage contracts more efficiently this way. A small firm with 50 people could have three CAGE Codes. They may not need to create three different SSPs if all three CAGE Code entities (CCEs) have the same controls and processes. They can create one SSP to support three CCEs.
CMMC for Multiple CAGE Codes
Can I use one SSP?
The DFARS Security Requirements do not specify a method for grouping CAGE Codes. It is up to you to determine how you would like to group your SSPs. You can group them by business functions, programs, the type of products you provide, etc. As long as you can articulate how you logically group the CAGE Codes and create a set of controls in an SSP to support them, you will be OK.
Where do I find my CAGE Code?
You can find your CAGE code at cage.dla.mil
Once you understand the CAGE Code(s) within your company, what they do, how DoD and your firm uses them, and how your company organizes and logically groups them, you will be able to create accurate CUI Scope and Boundary. This means you will be able to manage your SSPs efficiently and effectively. You will set your company up to gain more DoD contracts and win new valuable clients by registering your CAGE Code.
Here’s a summary of what you’ll get with us
KLC Consulting is an authorized Cyber AB C3PAO. We provide Cyber DFARS and CMMC Consulting services. We find the compliance efficiencies available to large companies with multiple CAGE codes. Opportunities exist through the inheritance of SSPs, controls, policies, and procedures among parent and subsidiaries. We specialize in Cyber DFARS and CMMC compliance. And our staff include Certified CMMC Professionals and Advanced CMMC Registered Practitioners with Fortune 500 experience in government contracting.
KLC Consulting helps create Cyber DFARS and CMMC compliance strategy for Fortune 500 companies.
Our Cyber DFARS and CMMC compliance strategy program for Fortune 500 companies includes:
- A 1-hour briefing delivered to the decision makers from each business division with time for q-a. They’ll come away with a high-level understanding of FCI, CUI, Cyber DFARS, COTS Exemptions, and CMMC requirements to inform their decisions.
- A review and summary of your DoD contract revenue by CAGE Code Entity. Efficiencies exist among parent-subsidiaries although each has Cyber DFARS and CMMC compliance requirements.
- A cost-benefit analysis of DoD contract revenue against the cost of a CMMC Gap Analysis for each CAGE Code Entity. This guides the decision on whether pursuing Cyber DFARS and CMMC compliance is a sensible business decision for each CAGE Code Entity.
- An evaluation of the optimal ways to inherit CMMC controls, policies, and procedures among CAGE Code Entities to minimize compliance program effort and cost.
- A product line review to consider COTS Exemption opportunities.
- A determination of the most efficient course to obtain BOTH CMMC Level 1 and Level 2 for CAGE Code Entities when required by Cyber DFARS and CMMC.
"*" indicates required fields
Video on CMMC for Multiple CAGE Codes
Today’s discussion concerns CMMC for Multiple CAGE Codes in large companies organized in a hierarchy of corporate structures. Companies grow through profitability and merger acquisition. These include large U.S. defense industrial base companies that manufacture and sell products to the Department of Defense. The DoD identifies and contracts business with companies by their unique CAGE Code. Company identification on a CAGE Code basis is similar to how the federal government uniquely identifies people by social security number.
Cybersecurity compliance with prescribed DFARS requirements likewise must be achieved for each CAGE Code. CMMC compliance for companies with multiple CAGE Codes requires additional considerations and strategy. But efficiency opportunities exist. U.S. DoD cybersecurity expert Kyle Lai discusses CMMC for multiple CAGE Codes and the best approach for large companies to develop their CMMC and cyber DFARS compliance strategy.
Video Introduction
[Kelly] Hello, everybody, and welcome to our talk today about CAGE codes, cyber DFARS, and CMMC challenges related to medium and large companies. I’m Kelly McDermott, your host today and founder and director of Heinz Communications s strategic marketing firm, and I also am a marketing consultant for KLC Consulting. With me today is Kyle Lai, president and CISO of KLC Consulting. Hello Kyle. [Kyle] Hey Kelly, how are you?[Kelly] I’m doing great; how are you?
[Kyle] Yeah, very good.
[Kelly] Good, Are you ready to talk about CAGE codes?
[Kyle] Yeah, absolutely, it’s a very interesting topic.
What is a CAGE Code
[Kelly] Yes, yeah, lots of a lot to unpack. So, thanks for taking the time to talk about this; more specifically, we will talk about how CAGE codes apply to medium to large businesses. And what they need to know, what the implications are of CAGE codes. By definition, CAGE code stands for “Commercial And Government Entity.” And if your company wants to bid on Government Contracting jobs, you must have a CAGE code. Isn’t that right, Kyle? You can’t do business with the government unless you have a CAGE code? [Kyle] That is correct, yeah. You must have a CAGE code to do business contracts or grants with the government. Yeah, the federal government specifically. [Kelly] Right. So, you can’t get out of the gate without one. And it would be an excellent start to talk about what is a CAGE code. What is it?Entities and CAGE Codes
[Kyle] Yeah. You must have a CAGE code if you own a company or entity and want to do business with the federal government. But before we start, what is an entity? Right, let’s get that definition out of the way first. So, in business terms, an entity could be a person or department within your company, corporation, or manufacturing organization. Any group that could do business or conducts business in the U.S. could be doing business with the federal government. So, that’s what we call an entity.And these entities can apply for a CAGE code. Right, so what is a CAGE code? If you are a U.S person and you file a tax return, the government is going to identify you based on your social security number. There could be hundreds or thousands of John Smiths if you’re John Smith. They won’t know who you are, you know, based on your name. So, they give you a social security number. So, in this case, the government will assign you a CAGE Code if you are doing business with them. And that will be how they identify to whom the contracts are given.
[Kelly] Kyle, is a CAGE code unique to each business, or is it unique to each entity?[Kyle] Each entity. So, a company with multiple departments could have multiple CAGE codes. You could have multiple CAGE codes. It depends on the business or the type of business that you do within the same company
[Kelly] Got it, great. So the larger the company, the more complex this tends to be – because there could be multiple CAGE codes?
[Kyle] Right, that is correct.
Large Companies and Multiple CAGE Codes
[Kelly] In today’s world, for example, a large company has 250 employees with 10 million dollars in Revenue. That’s considered a large company. Now, these companies have grown, and they have become more profitable. And they tend to become more profitable by acquiring yet another company to continue to expand.For example, suppose a company manufactures aircraft to sell to the government. In that case, they decide to acquire another company, a helicopter parts manufacturer, leading to many different business lines here. It’s like a hierarchy of business CAGE codes. So, what are the implications when a company expands like this? And now has a couple of different companies underneath its umbrella?
Each CAGE Code Must Comply with CMMC
[Kyle] The DoD’s DFARS and cybersecurity requirements aim to protect Controlled Unclassified Information, the CUI within the defense contractor’s Network and system environments, right? In a large company with multiple CAGE code entities, the DoD still expects each CAGE code entity to meet the cybersecurity and DFARS requirements. If you have a dozen or hundreds of CAGE codes, you should still find a way to consolidate these CAGE code entities into groups. So, if they share the same network and business processes, you can try to reduce them into a group and assign a system security plan to that group. You should then evaluate and see if creating one system security plan for the group of CAGE codes, you know, with the same business processes, makes sense.In your example, airplanes and helicopters are very different. There could be two groups and two system security plans (or SSPs). But our goal is to minimize the number of system security plans. When you’re talking about NIST, they have a development document about how you should develop the system security plan. But it does not explain or recommend how to establish the system security plan based on the CAGE codes. However, it doesn’t tell you too much about how you separate your CAGE codes or consolidate these CAGE codes. Because these CAGE codes are not discussed much within the industry or the system security plan.
Contract Management Know Your CAGE Codes
The company contract management people understand CAGE codes very well. And they know the hierarchy of the CAGE codes. But when it comes to I.T. or cybersecurity groups, they know about I.T. but don’t know about CAGE codes. So, these two groups should discuss organizing the CAGE codes. I.T. – they should understand how to manage the CAGE codes. And the contract Management Group should understand the cybersecurity requirements: How do we minimize the requirements that apply to these CAGE codes?
Every CAGE Code Entity Needs an SSP
Because each CAGE code needs to have a system security plan, and if you have one system security plan that can apply to as many CAGE codes as possible, that will be ideal for the company. That will save you time, money, and effort. I also want to point out that DFARS, cybersecurity requirements, and CMMC rulemaking are still under development. When it’s going to come out, we don’t know. But we know it’s going to be sometime in mid-2024. However, the DFARS 252.204-7012, with NIST 800-171, these requirements are not changing. All companies with defense contracts today must comply with these requirements. And they need to develop a system security plan. So, yeah, that’s why it’s crucial for you to create a CAGE Code compliance strategy; when you have multiple CAGE codes. Consolidate them into a few system security plans.
Consolidate CAGE Codes Into One SSP
[Kelly] You brought up some excellent points here, Kyle. One is the importance of communication within a company, so the I.T. department and the supply chain members in these groups talk together to understand the process. They need to comply, and the other thing too, to be efficient with this, like grouping them to maximize efficiency. You want to be efficient with how you do these groupings. And I think that’s an important point to keep in mind. So, the Cyber DFARS requirements for 7012 to protect CUI and 7020 to report the NIST 800-171 self-assessment results to the SPRS are on the books. So, let’s say, you know, those are done. Those are given. And those are not going away; to your point, those are in place and will stay. So, what steps are involved if a company has multiple CAGE code entities?Strategy to Consolidate CAGE Codes
[Kyle] You want to make a list to understand how many CAGE Code entities you have. So, that is the first thing you must find out. And after you find out the CAGE code, some of the CAGE code entities might only contract a small number of business contracts with the DoD. Then you want to understand how much money is each CAGE Code making from DoD. And the reason is that you want to have that number to determine if you should go through that long-term commitment. Are we going to spend the money and invest more in cybersecurity requirements? Do you need to have the certification required by DoD?That will be a different level, so, for example, I’m only making ten thousand dollars from DoD. Spending $70,000 may not make sense for this particular CAGE Code entity. So, we must understand the dollar value of the DoD contracts for each CAGE code entity.
Then also, you want to group the DoD contracts by the CAGE codes. And understand which CAGE code or which businesses with the CAGE code handle CUI, Controlled Unclassified Information. And you can find this easily within your contracts if you have CUI. Then that means that within your contract, you have DFARS 252.204-7012. You have FAR 52.204-21 if you handle Federal contract information. And you also want to make sure…
[Kelly] That’s easy for you to say.Commercial Off The Shelf Exemptions COTS
[Kyle] Right. And also, you might want to determine if you have some entities selling commercially off-the-shelf products. If you are not making any modification and qualify as a COTS, commercially off-the-shelf product C-O-T-S COTS, you are exempt from all these DFARS certification requirements. So, you want to explore that option as well. So, these are some things that you can do at this time to see how you should proceed for the future, for the long term. [Kelly] That’s great. That’s helpful, Kyle. Does it make sense for a company to determine whether they’re COTS exempt? [Kyle] It will be good to identify which CAGE Code entities could be exempt for larger companies because they are selling COTS products. But when you are talking about COTS products, this CAGE Code entity is selling commercial items. And you are selling it to DoD the same way as you’re selling to the general public General commercial, right, items. [Kelly] Right. [Kyle] also, you cannot modify products for the DoD. And you must charge them the same price. So, if you meet all these, these are very high-level qualifications. But if you go through this high-level qualification and the answer is yes, yep, to all these questions, maybe you can explore more and see if the CAGE Code entity sells the products qualified as COTS. It will be great if you figure out that first so you don’t spend the time, money, and effort.CMMC and Return on Investment (ROI)
[Kelly] Right, that’s excellent advice. And the other thing you said that I want to highlight is that you must assess the ROI with this. So, you need to consider – is there enough money in this to offset the cost of you making this commitment? And if it looks like you’re going to have more contracts and you’re going to open up, uh, expand your business by doing this, it would be worth it. But you do need to do that assessment first and figure out if, um, you know, if the value is there for you to go through this process. [Kyle] Yeah. It’s not cheap to go through all the cybersecurity certification requirements. So yeah, the earlier you know, the better. [Kelly] And in addition to that, if you do go through this and you determine that – yes – this is the way we want to go, you’re opening up to perhaps gaining more government contracts. When this initial review is all complete, what next?I.T. Considerations For Consolidating CAGE Codes
[Kyle] You need to develop a system security plan for each of the CAGE codes, so if you know how to group the CAGE codes, as mentioned earlier, then you can have one system security plan apply to different CAGE codes. So, you can try to minimize the number of system security plans. If you can use one system security plan for all of your CAGE Code entities, that would be ideal. It may not happen because they have to be on the same network and [have the] same business processes.So, if they are not on the same network, it will be hard to group them and say yeah, we have one system security plan for all these CAGE codes. So, you want to consider that as well. But just an example: if these CAGE codes all share the same I.T. services so you have the central corporate I.T. that provides the email, provides the cloud services, provides the antivirus, for example, these are the I.T. controls that can apply and be inherited to different system security plans. So, there are still many things that we can do to minimize the work.
Inheriting Policies, Procedures, and Controls
And [I] also want to say if you already comply with the other cyber security standards, for example, ISO 27001 or CIS top 18, top 20. If you have different policies and cybersecurity policies in place, you can inherit some of these policies; if you already have corporate cybersecurity policies and incident response plans, you can inherit these policies to minimize the work. Take whatever you can. And there might be other things you need to add to these policies, procedures, or plans. Add the other items to this policy and make it a corporate policy. I think that would be fine. So, that will be a way to minimize the work.
[Kelly] Okay, it sounds to me like you’re talking about I.T. vertical integration. Can you explain more, Kyle, and shed more light on I.T. vertical integration? [Kyle] Right. Example: there could be one I.T. group. You might have 100 different CAGE codes throughout two networks. But the way I.T. works, procedures, processes, and controls that I.T. implements are the same. Throughout various networks, throughout different – for different CAGE codes.If I.T. documented how we do things: this is how we track the changes, how we protect the networks, how we add the new user, monitor the malware attacks, how we monitor the logs, how we determine and mitigate the risk – a lot of these controls, if they are in place, and if they are the same for the I.T. controls, then we can apply them to different system security plans. And we can use [them] to other CAGE codes. So, in the way we are trying to inherit and apply these I.T. controls, we don’t have to rewrite them. Because they are the same, can we inherit them and reuse them.
Family Tree Analogy
[Kelly] Okay, thank you for clarifying – further clarifying that. It reminds me of a family tree. Where you have sort of the parents at the top of the family tree, if you will, and then you have the branches that lead out from that. And as long as everything is intact at the top, then all the other members, if you will, funnel up through that vertical chain. And they’re regarded as okay, as safe, as compliant. Is that right? [Kyle] Yes, yup.[Kelly] It’s a simplistic way of looking at it. [Kyle] Right, yeah. If you can inherit the controls from different entities or if there are shared common controls, policies, and procedures – you can inherit – try to do that in a large company because that will save you much time. [Kelly] That’s excellent advice. So, I see an added layer of complexity here with medium to large-size companies. And you want to get it right because, as you said, it’s an investment of time. It’s an investment of money. And you want to set yourself up to be in the best shape you can if you go through this process. All right, so you’ve done the analysis. How does a large company then group the CAGE codes?
Organizing CAGE Codes by CMMC Level
[Kyle] Different CAGE codes handle Federal Contract Information -FCI – or CUI – Controlled Unclassified Information. Or they went through the exemption right, COTS exemption. So, we want to group them based on the type of information, so if they handle FCI – Federal Contract Information – we identify them as CMMC level one certification. If they handle CUI – Controlled Unclassified Information – they must go for CMMC level 2. And based on the certification that you’re going for, if they are on the same network, you can further group them and create one system security plan. And for this group of CAGE code entities that handle CUI, the same network, and similar processes, we can group them separately and have a system security plan.So, as we mentioned, some companies will be going for the DoD contracts. They’re thinking about going for DoD contracts. But knowing the cost, they might want to stay with CMMC level one certification: we don’t want to touch any CUI contracts that handle CUI. We want to go with the DoD contracts but only handle Federal Contract Information at that level. Because it’s a lot easier for us to manage the controls, right? That’s meeting CMMC level one.
CMMC level one – it doesn’t require a system security plan. But I would suggest having a system security plan for CMMC level one because when the DoD finishes rule-making, CMMC level one will also require the senior executive – senior official – to sign off. Saying that, yup, our company CMMC level 1, we are meeting all the 17 controls. So, yeah, I would suggest creating the system security plan for level one [and] level two.
COTS Exemption from CMMC and Cyber DFARS
And for COTS: COTS – if you are qualified as [a] COTS vendor for some of the CAGE Code entities, you can get an exemption. But you want to make a list of entities within different groups, so you have an understanding of which contracts could be, you know, impacted by the CMMC and which group they should be going for. And how you organize it so you can have the system security plan divided up. And say this system security plan is for this group, and system security plan number two is for that group. So, you want to have that organization.
You won’t be able to validate the correct group organization unless you’ve gone through the scoping and the Gap Assessment. And understand which networks [are] on the same network: do they have the same business processes? So, you must go through the Gap Assessment and business process evaluation before you can determine – yep, these are the groups that we will put together for this system security plan and have that validation. So, some analyses need to be done. That’s the process you have to go through.
CMMC Final Rulemaking Considerations
[Kelly] Right. You brought up an excellent point about whether it’s CMMC level 1 or CMMC level 2. Eventually, you must do these things when the new ruling comes out. So, it seems it makes sense to do them now and get these controls and processes in place before that ruling in 2024. [Kyle] Yes. Whether CMMC rulemaking will be done on time, companies must still meet the DFARS 252.204-7012. So, the companies still need to analyze the CAGE Code and develop the system security plans for each CAGE code because that is still the requirement.Do CAGE Codes Expire
[Kelly] All right, thank you for that. That’s important to know. Speaking of controls and CAGE code management, do CAGE codes expire? [Kyle] CAGE Codes expire five years from the last update. So, go into your SAM – System for Award Management, SAM, S-A-M, sam.gov, to update your CAGE code.Cost to Obtain and Maintain CAGE Codes
[Kelly] Okay. And can you talk to us about the cost associated with CAGE codes? How much does this cost?[Kyle] Luckily, the CAGE Code registration and maintenance are free. We don’t know if it will be free forever, but at least for now, it is free. DoD, the Defense Logistics Agency, and DLA maintain it.
[Kelly] Hmm. Okay, that’s awesome. You don’t hear that too often.
[Kyle] Not these days, but we’ll take whatever we have now. [Kelly] That’s right. Well, I think this was an insightful conversation Kyle, about CAGE codes and large companies – medium to large companies. And it can be complicated to navigate your way through unless you understand the implications. As you acquire new businesses and grow and want to expand, these are important things to remember. As you mentioned earlier, KLC Consulting does help companies with this. And KLC provides the assessment and the blueprint, if you will, on how to become compliant. And eventually, win more contracts. So, reach out to us anytime with questions. If you want to learn more, please visit our website. And thank you, Kyle, for all your expertise today on CAGE codes and everybody for joining us today. [Kyle] Great, thank you.
