CMMC for Software Development Companies: We help you determine where you’re at in CMMC. And bring you all the way to “Assessment Ready” through flexible consulting services and today’s best CMMC technology solutions.
CMMC for Software Development Companies: Key Considerations
Defense software that handles Controlled Unclassified Information (CUI) requires “Adequate Protection” under cyber DFARS 252.204-7012. Which also means that certification in CMMC will be required, likely to begin in 2025
Here at KLC Consulting, we have specialized expertise in software development and CMMC compliance for software. Our goal is to make this process clearer and more approachable. Let’s talk about:
- Cloud Deployment Considerations: Important security practices you need to implement even when using trusted cloud providers.
- Collaborative Security: How to get your software development team on board with CMMC requirements.
- Secure API Design: Protecting the gateways to your software.
- Vulnerability Management Strategies for a proactive approach to security.
- Open-Source Management (SBOM): Handling those third-party components responsibly.
- Container Security Safeguarding CUI in your containerized environments.
Secure Cloud Deployment: It’s Not Automatic Compliance
Platforms like AWS and Azure provide you with a secure foundation, but they don’t automatically make your software compliant. Think of NIST 800-171 and CMMC as an added layer of security required by the DoD. They’re required even when running in a trusted cloud environment. This means:
- Secure Coding: Preventing vulnerabilities from getting built into the code.
- Vulnerability Scanning and Updates: Staying on top of security patches and fixes.
- Secure Deployment: Creating hardened environments for your software.
- Access Management: Controlling who sees and changes your CUI.
Software Development Teams: Essential to CMMC Compliance
Don’t make the mistake of thinking CMMC compliance is just IT’s responsibility. Your software developers need to be involved from the start. This helps ensure your software is designed with CMMC compliance in mind. It makes compliance much easier to achieve. Collaborate with them on:
- Understanding CUI Flows: Analyzing how data moves through your system.
- Reviewing Designs: Identifying potential security weaknesses early on.
- Managing Vulnerabilities: Having a plan for patching and updating your code.
Your APIs are “In Scope” for NIST 800-171 and CMMC
APIs are how your software talks to the world. They’re “In Scope” when they handle CUI. Secure API design means:
- Managing Access: Strictly controlling API keys and authorizations.
- Encryption: Protecting data that’s moving to and from your software.
- Vulnerability Prevention: Using best practices to prevent common API attacks.
Testing, Patching, and CMMC
- Testing Your Code: Regularly scanning for security flaws.
- Staying Patched: Applying updates to fix known vulnerabilities.
- Tracking Dependencies: Understanding security risks in third-party code used in your software.
Managing the Open-Source Landscape
Open-source software is great, but it needs greater attention regarding security. Staying CMMC compliant means:
- Knowing Your Components (SBOM): Maintaining a detailed list of the open-source libraries in your software.
- Staying Informed: Tracking vulnerabilities in the open-source world.
- Being Responsible: Complying with any licenses of the open-source code you use.
Container Security and CMMC
Containerization makes deployment easier, but for CMMC compliance:
- Scan Your Images: Checking for vulnerabilities before putting containers into production.
- Follow Best-Practices: Securing the environments where your containers run.
Need C3PAO caliber CMMC compliance help?
We often see that defense software companies incorrectly assume that putting their software in a secure AWS or Azure cloud environment means that it’s secure, and that they don’t need to worry about cyber DFARS and CMMC. It it handles, stores, or processes CUI, it’s in-scope of NIST 800-171 and CMMC.
If you have questions or need help with CMMC for your defense software projects, please get in touch with KLC Consulting!
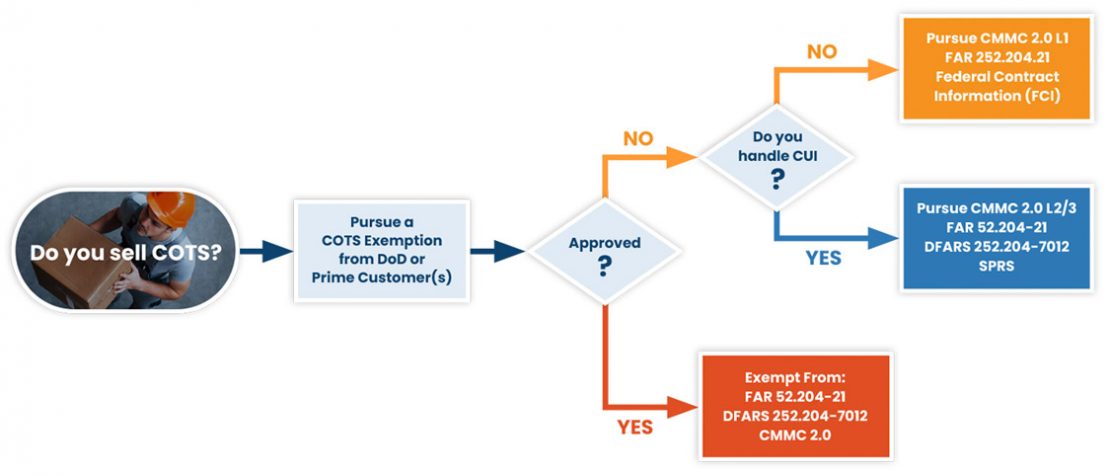
Are You a COTS Supplier?
Don’t assume CMMC 2.0 requirements apply just because you received one of the many compliance form letters sent out from your prime customers. The DoD created exceptions, and one is for “COTS” products. We can help you pursue a COTS exemption and avoid an unnecessary CMMC 2.0 Level 2 or 3 compliance program.
However, if you are not COTS, we provide consulting services to navigate you through the compliance process. Use our requirements flowchart below to help you determine if NIST 800-171 and CMMC 2.0 apply to you.
COTS, CUI, or FCI Determination Flowchart
CMMC For Software Development Companies Who Handle CUI
Background
$600 billion dollars or about 1% of global gross domestic product each year is lost through cyber theft. Adversaries know that in today’s great power competition environment, information and technology are both key cornerstones and — and attacking a sub-tier supplier is far more appealing than a prime.
Source: defense.gov
Because there are fewer controls over CUI as compared to classified information, CUI is the path of least resistance for our geopolitical adversaries. Loss of aggregated CUI is one of the most significant risks to national security, directly affecting the lethality of our warfighters.
Cybersecurity Regulatory Compliance Phase-In
December 31, 2017
The U.S. DoD requires Defense Industrial Base companies to provide “reasonable security” for Covered Defense Information, including CUI via DFARS 252.204-7012. Many small-medium size companies are slow to implement due to a lack of resources and technical expertise.
November 30, 2020
Compliance enforcement strengthens through interim rules (DFARS 252.204 -7019 & -7020) requirements to submit NIST 800-171 self-assessment results into the DoD’s Supplier Performance Risk System (SPRS). The SPRS enables DoD contract officials to consider a company’s self-assessment score (or failure to report it) in their contract award process.
Prime contractors seek confirmation from their subs about their compliance progress and status of their SPRS submission due to compliance flow down requirements.
DFARS 252.204-7021 ushers in CMMC (Cybersecurity Maturity Model Certification) that requires independent certification by an authorized C3PAO company.
November 04, 2021
The DoD releases CMMC 2.0 with the stated intention to simplify the CMMC standard while still safeguarding sensitive information. The previous 5 CMMC maturity levels are reduced to 3 and the number of controls is reduced to align with NIST 800-171.
What’s Next?
Determine if you handle CUI
If your software is not COTS, we look to your DoD contracts to determine if you handle Controlled Unclassified Information (CUI). If you don’t handle CUI, your DoD contract information is Federal Contract Information (FCI). You’ll only need CMMC Level 1.
Ok, you handle CUI
Your goal is to differentiate CUI from all other information you handle, segregate it into a dedicated and secure environment, and minimize its footprint. We ascertain the nature and category of your CUI through a review of the DoD’s CUI Registry. And we scope CUI within your business organization using our proprietary Data Lifecycle approach to reduce compliance effort and cost.
We offer a CUI Scoping service to begin your CMMC 2.0 compliance program.
Your progression from NIST 800-171 to CMMC
DFARS 252.204-7012, -7019, and -7020 require you to perform a NIST 800-171 self-assessment, submit summary-level score with POAM information to the DoD’s SPRS web portal, and remediate POAM deficiencies in pursuit of DFARS 252.204-7021 CMMC 2.0 Level 2 compliance.

SPRS DoD
Have you made your SPRS submission?
If you haven’t made your SPRS submission, we offer an affordable consulting package with a 30-day turnaround time.

CMMC Consulting
Have a low SPRS score? You’re not alone. Let us help you remediate NIST 800-171 POAM deficiencies and develop a CMMC 2.0 Level 2 compliance program just for you.

CMMC Gap Analysis
Want to confirm you’re ready for CMMC 2.0 assessment by a C3PAO? KLC Consulting evaluates readiness by simulating an independent C3PAO assessment.
CMMC for Software Development Companies: Challenges We Solve
- Compliance knowledge and the ability to remediate POAM deficiencies is low among IT and management staff
- Getting my staff trained in CMMC?
- Is my software supporting/hosting infrastructure is secure?
- How do I integrate security into my DevOps pipeline with minimal impact on my developers?
- What are good SAST, DAST, IAST (Static, Dynamic, Interactive Application Security Testing) Tools for my development environment?
- Good tools options to identify and mitigate open-source component vulnerabilities (software component analysis)?
- How do I verify and minimize container security risks?
- How do I ensure that my customers’ solutions are compliant with CMMC/ NIST 800-171?
- Does my incident response plan comply with DFARS 252.204-7012 requirements?
- Do I need to get FedRAMP certified? And at what level?
- Are my tools certified to support CMMC/NIST 800-171?
- Uncertainty about flow down compliance requirements to subcontractors
- Uncertainty responding to compliance-related questions from:
- DoD agencies
- Prime contractors
- Subcontractors
- Cybersecurity insurers
- Incident response planning and reporting (DFARS 252.204-7012)
- Incident response plan testing (tabletop exercise)
- Penetration testing/vulnerability testing





