
Top Cybersecurity Threats Defense Contractors Face in 2023
By Kyle Lai
President and CISO, KLC Consulting
- Pending: PI (Provisional Instructor)
- Pending: PA (Provisional Assessor)
- CISSP, CSSLP, CISA, CDPSE, CIPP/US, CIPP/G, ISO 27001 Lead Auditor

Introduction
Companies that sell to the U.S. Department of Defense are working to improve their cybersecurity posture in anticipation of CMMC requirements. With final DoD CMMC rulemaking expected in 2Q 2023 (1). CMMC clauses will begin to appear in DoD contracts in the calendar quarters after that.
The DoD ushers in CMMC amid the most challenging of times for information security in my 25-year career. But the greatest cybersecurity risks to the prime contractors won’t come from direct attacks to steal information and disrupt their business operations. Instead, the greatest cybersecurity risks to prime contractors will come from their valued subcontractor business partners. Cybercriminals know that large prime contractors work diligently to improve their cybersecurity posture. But their small-medium size subcontract partners? They’re hit or miss. Many continue to utilize unsupported legacy I.T. systems and are well behind the current cybersecurity requirements of DFARS 252.204-7012 and -7020.
How Subcontractors Unwittingly Create Risk
Here’s a scenario I’ve witnessed play out time and again:
DoD prime contractors often receive emails from subcontractors they know. So, they’re used to opening them and clicking on file attachments. But when a cyberattack has compromised a subcontractor’s email system, the prime employee unwittingly opens the door and initiates a cyberattack.
This recurring theme is why we often hear from our new small-medium size Defense Industrial Base clients:
“We received letters and questionnaires from our prime customers. They need to know where we’re at with our DFARS 252.204-7012 and -7020 requirements because we handle their CUI. And they’ve told us we’ll lose our contracts if we don’t meet the new CMMC cybersecurity requirements – we need help.”
Beyond Flow Down Requirements
The 80,000 Defense Industrial Base companies have heard the steady drumbeat of “Flow Down Requirements” to protect Controlled Unclassified Information since the DoD established the interim DFARS rules in November 2020. But the requirements come amid a high-threat environment during the most challenging times in cybersecurity. I am keen to stay on top of the rapidly changing cyber threat landscape to best serve my clients.
The Top 6 Cybersecurity Battles Defense Contractors Face in 2023
1. Severe Disruptions in Cloud Service
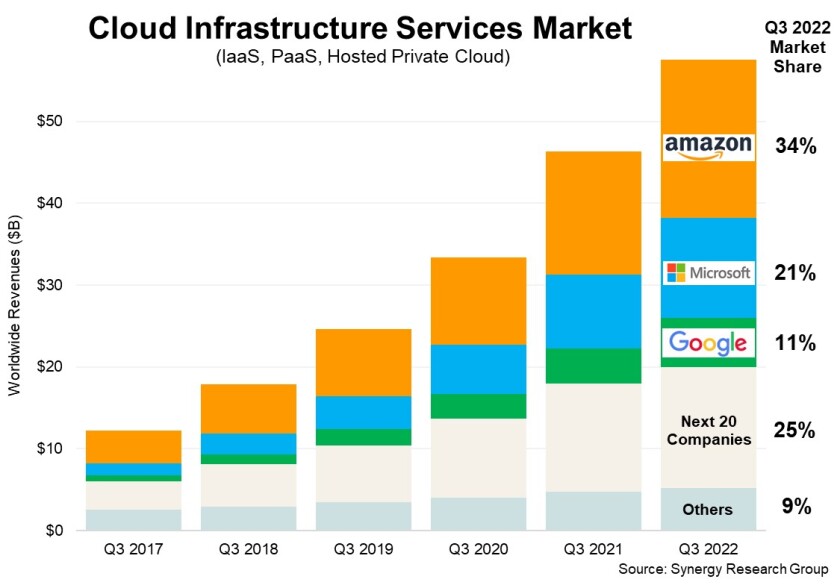
Major cloud service providers (CSPs) such as Azure, AWS, and Google own 66% of the market share (chart: Synergy Research). Software as a Service vendors such as Akamai, Cloudflare, Slack, and Atlassian’s Jira also serve most Government agencies and medium to large companies. Attackers know that weak password protocols, misconfigurations of cloud security settings, and human errors continue to be the leading causes of cloud data breaches. (2)
How to Reduce Impacts from Cloud Service Provider disruptions
- Minimize the single point of failure
- Implement a business continuity plan
- Perform regular backups, and ensure recovery capabilities
- Monitor and detect CSP outages ASAP
- Host your data in multiple regional data centers
2. Rise in Aggressive AI-Driven Cyberattacks
Artificial Intelligence (AI) based penetration testing tools and attack simulations have become increasingly sophisticated. (3) Attackers are taking advantage of the power these tools offer. In response, technology solution providers are building AI and Machine Learning capable tools used in more advanced cybersecurity programs. Examples include Antivirus/Antimalware, data loss prevention, fraud detection/anti-fraud, identity and access management, intrusion detection/prevention system, and risk and compliance management (4).
But cyberattacks are narrow and focused while defending against them is broader. Expect cyber attackers to achieve success through more targeted attacks, especially in less advanced cybersecurity programs.
We’ve entered the machine-against-machine era.
3. Software Vulnerabilities Proliferate
Ask your staff: They’re overwhelmed with applying security patches for your I.T. infrastructure.
I.T. used to anticipate Microsoft’s release of security patches on “Patch Tuesday,” the 2nd Tuesday of the month, to correct the latest discoveries in security deficiency. In the past few years, other vendors such as Adobe and Oracle published software patches simultaneously with Microsoft. Cyberattackers adapted to “Patch Tuesday” defense tactics by creating “Exploit Wednesday,” to take advantage of serious vulnerabilities knowing companies are typically slow to patch. (5) Beyond Patch Tuesday, software companies also publish emergency patches for high-risk vulnerabilities more frequently.
The magnitude of software vulnerabilities often exceeds the I.T. staff’s ability to fight them. Technology solution providers are developing and selling solutions to help, but they can’t come quickly enough. And many small-medium size subcontractors are unaware of affordable options to help prevent a data breach. (6)
4. I.T. Staff Morale Stagnates
In addition to their daily responsibilities, I.T. and cybersecurity staff manage activities like emergency patching, security event/incident investigation, security tools implementation, third-party risk management, RFP response, customer cybersecurity inquiries, and more. While I.T. and Cybersecurity groups frequently must beg for more resources to handle escalating demands, companies typically view the associated costs as unwelcome overhead. Needs go unfulfilled. Overwhelmed staff feels compelled to put in unsustainable heavy overtime that compromises work-life balance, leading to burnout and morale stagnation. (7)
5. Companies Drop Cybersecurity Insurance
We buy an insurance policy as a cost-effective means to mitigate risk. Cyber Insurance became “a thing” a few years ago as ransomware and data breaches skyrocketed. But Insurers quickly got wise to companies buying Cyber Insurance to avoid the cost of developing a good cybersecurity program.
But consider the parallel in the automobile insurance industry when a customer chronically drives recklessly. Rates increase, and eventually, the insurance company declines to renew the policy.
In today’s cybersecurity pandemic, customers must demonstrate that good security controls exist or face astronomical premiums and shrinking coverage. (8)
6. Cyberattacks Disrupt Supply Chain
“The Department of Defense relies on the entrepreneurial companies and innovative, hard-working employees of the Defense Industrial Base (DIB) to create cutting-edge capabilities for our warfighters.” – John Sherman, CIO for the Department of Defense (9)
Do you know which companies are critical to your supply chain? How mature are their cybersecurity protections against attackers? You should gather the answers ASAP if you don’t know them already. I’m optimistic overall, but I expect cyber incidents to cause significant disruptions in the U.S. supply chain in 2023 and beyond.
I recently achieved the CCP designation (Certified CMMC Professional) and my company, KLC Consulting, became a cleared candidate C3PAO. We anticipate becoming a fully authorized C3PAO during mid-2023. But today, only 32 companies are fully certified by the DoD. That number increases by a few during a typical calendar month, but the DoD sets rigorous education and certification requirements so building the ecosystem remains a slow process. The simple arithmetic is: It will take years for the 80,000 US Defense Industrial Base companies to become certified in CMMC.
My 6 Recommendations
1. Complete your DFARS 252.204-7012 requirements
- Get professional guidance with your NIST 800-171 self-assessment.
- Implement a cyber Incident Response Plan.
- Do employees know what to do when a cyberattack occurs?
- When to notify law enforcement? The DoD?
- Should you pay a ransom when a breach occurs?
- Have you purchased an ECA certificate to enable DoD reporting?
2. Complete your DFARS 252.204-7020 requirements
- Submit info to DoD’s Supplier Performance Risk System.
3. Prioritize your POAM efforts
4. Achieve certification in CMMC Level 2 ASAP
- Reap the business benefits of early compliance
5. Implement affordable CMMC technology solutions
- Solutions for CMMC compliance that deter cyberattacks and prevent breaches.
6. Implement a Business Continuity Plan
I often find new clients who haven’t developed a Business Continuity Plan. A case in point with a more recent Defense client:
They have an onsite diesel generator for backup electricity during a power outage. However, they didn’t develop a Business Continuity Plan that included periodic testing to verify the generator’s functionality. They lost power for two days in early 2022 during a nasty snow & ice storm, and, you guessed it, their generator failed. Beyond the $30k in physical facility damage caused by the freeze-up, they lost $252k in revenue due to a cessation of manufacturing operations.
So, do you need Business Continuity Planning?
You can’t afford NOT to!
References
- Multiple public statements from Stacy Bostjanick, Director of CMMC policy at DoD’s Office of the Under Secretary of Defense for Acquisition and Sustainment. One is available here on govconwire.com, posted by Summer Myatt.
- Verizon 2022 Data Breach Investigation Report pg 8
- 311 Institute: “Breakthrough AI Hacking Tool Cracks Millions of User Passwords in Minutes” by Matthew Griffin
- CNBC Technology Executive Council Report: “Artificial intelligence is playing a bigger role in cybersecurity, but the bad guys may benefit the most.”
- Forbes.com: “Google Pays Chrome Hackers $45,000, Releases High-Severity Security Update” by Davey Winder
- I often recommend Anchor as an effective, affordable file security solution to prevent data breaches.
- Forbes.com: “Burnout And Staffing Shortages: Looming Cybersecurity Crises That Need More Attention” by Nick Espinosa
- Kyle Lai – Personal experience through hundreds of client consultations.
- TheInformation.com: “Companies Are Ditching Cybersecurity Insurance as Premiums Rise, Coverage Shrinks” by Aaron Holmes.
- BusinessInsider: “Defending the defense industrial base from cyberattacks requires more cooperation with industry” by John Sherman, CIO for the U.S. Department of Defense.
NIST 800-171 & CMMC Resources
If you’re looking for the most comprehensive listing of NIST 800-171 and CMMC Resources available today, you’ll want to bookmark this page! We’ve aggregated all the most useful resources right here
- Cybersecurity Training (Free and Paid)
- FIPS 140-2/FedRamp validated product searches
- Policy templates
- Authoritative DoD cybersecurity pronouncements
- and much, much, more

Speaking Engagements and Training
With over 7,000 followers on LinkedIn, Kyle is a popular expert cybersecurity keynote speaker, guest lecturer, and CMMC trainer. Speaking engagements and training sessions are available onsite and virtually. Inquire at [email protected] for more information.


