Featuring Kyle Lai of KLC Consulting and Scott Armstrong of Exostar!
Hosted by Exostar on 04/28/2021
Greetings! And Welcome!
Scott: Good afternoon everyone, welcome to today’s session. The topic is NIST 800-171 and CMMC insights from a C3PAO candidate company. Kyle Lai is our special guest here today. I’ll do some housekeeping before we get into the presentation: Today’s webinar is scheduled to last between 45 minutes to an hour and that includes Q-A. I muted all participants to enable the speakers to present without interruption. A large portion of today’s event is dedicated to answering the pressing questions from the audience and these have been submitted prior to the event.
In the event of a service outage please wait for a minute and refresh the page. Luckily, we’ve not had that happen yet. For your convenience there’s a link in the YouTube description to a glossary of commonly used terms, acronyms and initializations that’ll be referenced during today’s webinar. We’re also going to record this session so it’ll be available on demand via our resource library. And as always if you want to speak to one of our industry experts or request a copy of this slide deck you can reach out to us at [email protected] or use our live chat feature.
Webinar agenda
Scott: First the agenda. So, this is all about the pathway to CMMC DoD and Kyle Lai will present. He’ll walk us through these topics from the perspective of his firm, which is both a consulting firm and a CMMC-AB cleared C3PAO candidate. We’ll follow with a Q-A session based on the pre-submitted questions, and as I mentioned there will be an exit poll at the end. My name is Scott Armstrong, senior director of our risk applications here at Exostar.
[The PDF of today’s presentation is available for download here]
And Kyle Lai is the president and CISO of KLC Consulting, and one of our CMMC consulting partners at Exostar. He architects solutions for NIST 800-171 and CMMC DoD compliance for DIB companies. He has over 20 years of cybersecurity experience with Fortune 500 companies, the Department of Defense, and companies within the DIB. You can see from his background he’s got a lot of DoD experience in cybersecurity and a lot of technical depth. Kyle holds the CISSP and CISA professional certifications among a dozen other credentials. He possesses advanced skills in the area of cyber security compliance especially when it comes in the realm of DoD requirements.
Featured C3PAO candidate expert – Kyle Lai
Kyle: Great, thank you Scott for your gracious introduction. In today’s discussion we’ll present an overview of the journey to CMMC and NIST 800-171 compliance. I’ll explain the key terminologies like CUI, FCI, NIST 800-171, DFARS, and CMMC. Before we get into the details, I’ll explain the relationship between NIST 800-171 and CMMC, and why the DoD established CMMC. And I will explain how to know when your company is CMMC “Assessment Ready”.
Best of all, I will share one of my “Cybersecurity Expert Tips” with you at the end of my presentation. This tip will help you save time and effort which translates to saving money in becoming CMMC level 3 ready.
This tip alone will be worth your time spent here listening to me today!
Terminology definitions
Let’s dive into the definition of CUI and FCI. My PowerPoint [here] shows the formal definitions. Informally, CUI is Controlled Unclassified Information. Please know that CUI is not classified information. But CUI is important, so you need to understand what it is. CUI requires protection because adversaries may aggregate it from different sources. And somebody could put CUI information together to construct “Classified Information”.
Here is an example: You are a welder and welding assemblies onto the wing of an F18 aircraft. You receive the technical drawings of the wing, this is CUI. And other companies produce parts and assemblies for it too. And there are drawings of other sections of the plane: The body, the tail, the cockpit and all the electronics. Individual drawings are CUI. A political adversary could steal the drawing from different contractors, put this all together, and figure out how to build the complete F18 aircraft. And this aggregates to become classified information. That’s why we protect CUI.
And federal contract information (FCI) is non-public, unclassified information. The DoD specifies controlled information within federal contracts and designated as non-public, meaning it is not intended for public release. An example is a statement of work or quality assurance plan. Next slide please.
Official DoD links to the CUI registry and CUI training
Here are some official links, this one is the DoD CUI registry. It lists out all the different categories of CUI. This one is a link to CUI training. But more importantly there’s one for mandatory CUI training which should be taken by all DIB company staff who handle CUI. One section of the CUI registry is about defense. So that’s what we call Covered Defense Information – CDI. It covers four different categories of defense information – Controlled Technical Information. The critical infrastructure security information and the nuclear information but most of the defense contractors will probably focus on CTI the Controlled Technical Information. On the right side you will see some examples of CTI, like technical drawings specifications, technical reports or source code.
Okay, next slide please.
(Questions about NIST 800-171 and CMMC? Contact us for more information)
DFARS regulations and their relationship with NIST 800-171 and CMMC
Let’s go through some of the basic cybersecurity lingo here:
DFARS is “the law”
- DFARS is the Defense Federal Acquisition Regulations. Think of DFARS as “the law”. DFARS clauses are included in defense contracts and you must comply with them. For the sake of clarity in our conversation today I will abbreviate the complete DFARS clauses into the last four digits. For example DFARS 252.204-7012 is a mouthful, but I will simply refer to it as DFARS 7012, so let’s just start with that one.
- DFARS 7012 became effective in December 2017. It requires DIB defense industrial-based companies to follow the NIST 800-171 cybersecurity standard. And it requires you have an Incident Response Plan to handle and report cyber incidents and breaches
- DFARS 7019 and 1720 cover the assessment methodology published by the DoD. It also establishes a mandate to report the NIST 800-171 self-assessment results to the DoD SPRS system. And DoD reserves the right to audit [you]
- And DFARS 7021 is CMMC DoD. CMMC is the acronym for Cybersecurity Maturity Model Certification. It builds on the NIST 800-171 standards foundation. It has 20 additional controls or practices plus additional documentation requirements. CMMC has five progressive maturity levels. Maturity level three is the minimum requirement level for DIB companies who handle CUI. Many of you here today are likely working with companies who handle CUI. And CMMC is being phased in during calendar years 2021 through 2025. All DoD contracts will require CMMC certification starting in 2026
NIST 800-171 and “Flow Down Requirements”
- NIST 800-171 is the cybersecurity standard for defense contractors or subcontractors. It is designed to protect CUI information within their information systems.
- Flow Down Requirements to your subcontractors: That means that you need to take measures to ensure your subcontractors with whom you share your CUI and FCI are also CMMC DoD compliant. If they are not compliant – neither are you! So the flow down requirements apply within DFARS 7012, 7019, 7020 and CMMC.
More about DoD regulations and COTS definition
So, this slide is an overview of the different regulations that define the terms and promulgate the standards I’ve just mentioned. And NIST 800-171 is the foundation that undergirds DFARS 7012, 7019 and CMMC DoD. On the top you will see 52.204.21 with its requirement to protect FCI, which also feeds into CMMC and becomes part of the requirement.
There are compliance exceptions to these rules if you are a contractor who strictly and only handles Commercial Off-The-Shelf products. You cannot just claim that on your own. That decision must come from your contract officer or your customer program manager. The government has a more detailed description and definition of what’s COTS or Commercial Off-The-Shelf. But the high-level understanding is commercial items without modification. And you must produce them at a large quantity and they must be publicly available. Okay next slide please.
NIST 800-171 is the current standard for protecting CUI
So, NIST 800-171 is the current standard for protecting CUI within the contractor’s systems. It has 110 controls. It allows you to be compliant with a Plan Of Action and Milestones for deficiencies. What does that mean? It means that you can be compliant while you still have deficiencies. You must document your deficiencies into a POAM, (Plan Of Action and Milestones). This shows how and when you will remediate your deficiencies. So in NIST 800-171, it requires you as a contractor to develop a System Security Plan (SSP). And your SSP must include your:
- CUI scope
- Boundary diagram
- Roles and responsibilities
- Inventory of your in-scope systems
- Documentation of the procedures and measures to address these 110 controls or practices
- And you need to document the POAM as mentioned earlier
If you have deficiencies, your POAM documents them and describes your plan to remediate them. It should also estimate the time frame during which you will complete remediation. Next please.
CMMC overview
Okay, here’s an overview of CMMC DoD. CMMC level 1 has 17 practices. It does not require documentation but obviously it will be best if you have written policies and procedures. CMMC level 3 has 130 practices. It does require documentation and as mentioned earlier, is the minimum level required for handling CUI.
Here are your two important takeaways:
CMMC Requires an independent C3PAO assessment…and there is no POAM!
- Unlike the self-assessment approach of NIST 800-171, CMMC requires assessment by an independent organization – what we call C3PAO, a CMMC third-party assessment organization like KLC consulting. We are a cleared C3PAO candidate, and will become an authorized C3PAO after we complete our own DoD assessment. At that time we will be fully approved for CMMC level three. So we must go through the same rigorous process that you must go through.
- And most importantly there is no POAM allowed in CMMC DoD. You cannot have any deficiencies and become certified in CMMC. Assessments are pass or fail. If you miss one control you will fail your assessment. So you want to be 100% confident that you will pass your assessment before you hire a C3PAO to assess you.
A C3PAO assessor will check your readiness prior to assessment
When you hire a C3PAO they will first check to see if you are ready for assessment before they begin. They will not start the assessment unless they think you are ready. And why is that? Because if you aren’t ready, you are likely to lose three to six months of your time and effort because you will need to go back and remediate your deficiencies. This would require more time, effort and cost. And that’s the last thing you want.
The evolutionary progression from NIST 800-171 to CMMC
So, why was CMMC created? Don’t we already have DFARS 7012 and NIST 800-171? Why do we need CMMC DoD? It is because the DoD Inspector General determined that defense contractors and subcontractors have not performed their NIST 800-171 self-assessments thoroughly and accurately since it became a requirement in December 2017. We’re not talking about the large companies like Boeing or Lockheed, the concern is with small medium-sized DIB companies. They lack adequate information security staff and expertise. But the DoD requires assurance that only DIB companies with sufficient cybersecurity maturity will handle CUI. So CMMC DoD is a higher standard built on top of 800-171 and has 20 added controls, as I mentioned earlier.
By the way the next version of CMMC will be out in May or June this year 2021. So, in the next couple months some things will change. Next slide please.
The 5 maturity levels of CMMC
We created this infographic to show you the 17 capability domains of CMMC. And there are the five different levels of maturity within CMMC DoD:
- One is for handling FCI
- Three and above for handling CUI
- Two is only a transition between one and three so many companies will ignore it
- Four and five are for a smaller number of companies that are more likely to be targeted by the nation-state threat actors so there are going to be a lot more practices required for these levels
The next slide please.
DFARS 252.204-7012 explained
This slide gives you more clarity with DFARS 7012. DFARS 7012 requirements already appear in DoD contracts that involve handling CUI. It requires the performance of a NIST 800-171 self-assessment to protect CUI. Plus it requires Incident Response handling and reporting capabilities.
Here’s something important for you to know: You are required to report discovery of a cyber incident to the DoD within 72 hours. And the DoD cyber incident reporting process requires you to possess a DoD issued certificate. So, either you designate an employee that already has a DoD common access card (a CAC card). Or if you don’t have a CAC card, you must obtain what’s called an ECA, or medium assurance certificate for each cage code you do business through. If you don’t have one, you must apply for and buy an ECA certificate through the cyber incident reporting site. And you can find more information here:
Purchase an ECA Certificate Here
The cost is just under $400 for three years. Next slide please.
Journey to CMMC DoD Level 3
This slide gives an overview of your journey and process to CMMC DoD maturity level three. You begin by scoping CUI within your business environment: Understand all your systems, devices, databases, applications, and cloud services that touch CUI. And perform your NIST 800-171 self-assessment. Next, submit your results to the DoD’s SPRS system. SPRS submission requires that you’ve developed your SSP, POAM, and determined when you’ll fix all the deficiencies listed in your POAM.
NIST 800-171 self-assessment net score explained
Let me briefly explain how the net assessment score works. A perfect score is 110. Each of the 110 controls has an associated point value of either one, three, or five points, as defined by DoD. Points are deducted for each unimplemented or partially implemented control, so your calculated net score is your summary level assessment score.
We often see organizations begin remediation with a negative assessment score. Remember that you need to develop and maintain an incident response plan as mentioned before, and obtain an ECA certificate. Remediate all your deficiencies in accordance with your POAM to become fully compliant with NIST 800-171. After you submit to the SPRS, you are in compliance with DFARS 7012, 7019 and 7020.
Now you are ready to advance to CMMC DoD and you should be in pretty-good shape if you’ve already addressed the 110 controls and meet your incident response requirements.
CMMC gap assessment
I advise performing a CMMC gap assessment to understand the remaining practice items you need to complete. And you should now be able to quickly complete all the CMMC practices. You have the option to hire a different C3PAO to do this gap assessment. (This will be a different C3PAO than the firm who will do your final assessment). The Gap Assessment C3PAO will be able to give you an opinion on your readiness for your final assessment. After the gap assessment, you can feel confident that you’re ready for the final CMMC assessment.
Plan to achieve CMMC DoD compliance early if you intend to bid on a contract with CMMC requirements. Okay next slide please.
How to know when you’re ready for CMMC Level 3 assessment
Here is a guideline we’ve developed to help you know when you are ready for your CMMC assessment. You’ll want to address the practice assessment objectives for each practice. I will show you an example on the next slide.
Your MSP and the Customer Responsibility Matrix
This is an area I haven’t talked about yet: Cloud service, and managed service providers, your MSP’s. If you use cloud service providers or managed service providers, request what’s referred to as a “Customer Responsibility Matrix”. They should be familiar with NIST 800-171 and CMMC, and be able to provide you with a customer responsibility matrix for all the practices and controls their service covers:
- Which practice areas are the service provider’s responsibility
- Which ones (practice areas) are your responsibility
- And which ones are shared responsibility – meaning that the controls must be implemented by both you and the service providers to make them effective
And get the details for these practices; how your service provider implements these practice areas, because it’s important that you inherit and incorporate their practices into your SSP. Next slide please.
About CMMC Practice Assessment Objectives
On this slide we have an example of “Practice Assessment Objectives”. These are from the CMMC level 3 assessment guide. In this case there are six assessment objectives from [a] to [f]. Each of the assessment objectives must be implemented for the practice to be considered effective and meet the requirements. Next slide please.
Final preparations for CMMC Level 3 assessment
Let’s talk about the final CMMC DoD assessment process before hiring a C3PAO for your final assessment. Confirm that you have documentation for all 130 CMMC Level 3 practices AND possess the required evidence. Make sure you have the evidence to document that you are compliant with all the 130 practices before hiring a C3PAO to perform the independent assessment I mentioned earlier.
CMMC-AB evaluates and certifies C3PAO assessment packages
Based on current understanding, the CMMC-AB (the accreditation body) will evaluate the submitted C3PAO assessment package and issue the CMMC DoD certificate. There’s talk that this process may change, but as of today that’s the process. Please note that C3PAO assessment and the CMMC-AB review will take about three months, give or take, but the actual duration will vary based on:
- The size of your in-scope systems,
- Number of devices,
- and Number of Applications,
- Complexity of your environment,
- The number of sites,
- and location of your sites
You’ll want to plan accordingly.
Your C3PAO can perform your assessment OR provide your compliance consulting – but not both
And also know that a C3PAO can either provide consulting OR conduct the final CMMC assessment but they cannot do both because doing both is considered a conflict of interest.
A big money saving tip from a CMMC C3PAO expert!
Before I end the presentation, I’ll share my “Cybersecurity Expert Tip” I mentioned earlier. Many small to medium-sized companies undertake their compliance effort on their own, to save money. They start by filling out an SSP template. And unfortunately, many consultants make the same mistake too.
This is the WRONG way to start, it’s the WRONG approach. Why? Because compliance is NOT about your entire company! It is about your company’s CUI! So, the correct starting point is for you to understand what your existing CUI is, and the CUI you plan to handle in future DoD contracts – if you’re looking at new contracts. DoD contracts specify information designated as CUI, and list the DFARS requirements you must meet. If you aren’t clear, get clarification from your contract officers about the type of CUI information you’ll be expected to handle.
Segregate CUI within your business environment
So, begin by understanding your CUI. THEN, you differentiate and segment your CUI data from your non-CUI data within your company’s environment. Your goal is to minimize the CUI scope and boundary. In other words – you want to minimize your CUI footprint. Again why? Because CUI compliance does NOT need to be a company-wide effort! And by reducing your CUI footprint, your compliance effort and cost will decrease significantly! CMMC, DFARS and NIST 800-171 compliance only apply to where CUI touches your people process and technologies. So they only apply to the systems that store, process, and transmit CUI.
Minimize your CUI footprint!
I recommend this tip because every day, and I mean literally every single day, people contact us about helping them with CMMC and DFARS compliance. And they say: “You’re the first consulting firm to tell us this! [the importance of CUI scoping and minimizing its footprint to save time, effort and money] So now that you know, our approach must seem obvious! It is to us! It’s also required by NIST 800-171 and CMMC. But the importance of CUI scoping to minimize it’s footprint and cost comes as a refreshingly novel and elegant approach for the companies and consultants we talk with.
Use KLC Consulting’s proprietary CUI Data Lifecycle methodology to scope CUI and minimize its footprint!
So, to that end, we’ve developed our own unique and proprietary methodology: It’s KLC’s CUI Data Life Cycle Methodology, which is our approach for scoping CUI. These are the six steps:
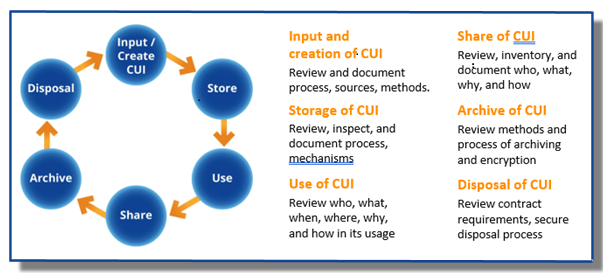
- CUI input creation. Understand how you receive CUI data, how it comes into your environment, and how you create CUI information
- Storage. Understand where your CUI is stored, how it’s managed, is it stored securely, who is managing its storage
- CUI usage. How do you use CUI, why do you use it, what system devices, databases and applications use CUI; and who within your organization (groups or business units or roles) are using your CUI
- Sharing of CUI. Who do you need to share CUI information with? Do you have a list of subcontractors? And how do you share it with them? What systems do you use to share it with them? Do you share it securely? And also, you share CUI information back to your prime contractors or the DoD, so do you share it securely back with them too?
- Then there’s CUI archiving and backup. Do you back up your CUI somewhere? Are your backups encrypted?
- The final step of the lifecycle is Disposal. CUI must ultimately be disposed properly and securely so no one can put it back together
KLC’s CUI Data Lifecycle methodology saves you time, effort and money!
KLC’s process will help you quickly and clearly identify your CUI and it’s scope. By reducing your CUI scope, you save time, effort and money. If you are working with a consultant who hasn’t told you about the critical importance of scoping and minimizing your CUI footprint, you definitely should ask them about it. And if you are interested in learning more about CMMC DoD compliance efficiency I welcome the opportunity to talk with you.
Hopefully you learned something new about CUI, NIST 800-171, DFARS -7012 -7019 -7020, and CMMC DoD compliance through my presentation. If not, I hope you use the tip I shared. It will help you properly define your CUI scope and save you time effort and money.
Please feel free to contact me if you have any questions, or if you need help with CMMC DoD, or your NIST 800-171 effort.
NOTE: KLC provides consulting help with understanding and scoping your CUI. Click HERE for more information
Scott affirms the critical importance of understanding CUI and its scope
Scott: Thank you, that was great Kyle! And that was excellent advice about CUI scoping. The DoD through the CMMC-AB is supposed to publish additional scoping guidance in the Summer time frame from what I understand. Yes, understanding CUI and its scope is step number one – if you want to minimize your cost, you want to minimize and constrain your environment. I totally agree with that, that was wise advice! Thank you!
Question and Answer segment of the webinar
Now we’ll move onto the Q-A section. We’ll make this slide deck available if you reach out to us afterwards and this will also be available as a recording. We also have links to several of the sources, some of which Kyle already mentioned, but also the steps for SPRS reporting. how to go through that process. Because that’s not necessarily an intuitive process either so this will all be in the slide deck. If you need it just request it and we’ll provide it.
Moving on to the Q-A, let me pull up some of these questions.
Question: About CUI Marking and Labeling?
I’ll start with question #3: The profile of the company is – they’re a software development company who provides logistics support to a DoD contractor, and are curious about the CMMC DoD requirements for marking media and limiting it’s distribution. That seems to be a real challenge. Do they need to tag all of their CTI information? All their design analysis and documents? And what about the software they’re developing, how should they deal with that from a CUI perspective?
Kyle: There are different ways of marking the on-screen display. Without knowing too much about how your application works, I would suggest you go to ISOO for training in how to deal with CUI marking for media, paper, and on screen. They offer training on the ISOO website.
NOTE: KLC provides consulting help with automated solutions for CUI marking and labeling. Click HERE for more information
Question: COTS, and can CMMC Level 1 be attained through a self-assessment?
Scott: I’m looking at a question number six. It’s from a company who believes they’re solely a commercial off-the-shelf manufacturer, a COTS supplier with the EAR 99 export classification. So it’s a two-part question: Can they perform their own level one assessment? And is a level one self-assessment sufficient? But what do they need to do to get a level one certification? Can you give any guidance on that?
CMMC DoD Level 1 requires independent assessment and certification
Kyle: Yeah, I think I touched on this in my presentation. If you are a 100 percent COTS supplier, you should seek a waiver from your prime or your DoD contract officer. Because it’s really not for you to decide if you can waive CMMC assessment requirements. Get a waiver so you don’t have to worry about CMMC DoD. Ask them about the CMMC level that you need. But if you’re trying to show that you are 100% COTS, you need to clearly understand the definition of COTS, be able to show evidence that this is all you do. And request the contract officer or prime contract program manager give you a waiver.
Scott: Yep now I will remind folks – if you think back to Kyle’s slide about some of the language about level one – if you’re doing direct contracting with the government, even on the civilian side, the controls that you’re already doing; you might not be required to get that level one certification but it certainly doesn’t hurt. And it helps reinforce that you’ve got those practices in place.
Note: All CMMC maturity levels require independent assessment from a C3PAO (even level 1)
Question: CMMC implementation methods for engineering drawings?
Next question: Can you speak to the implementation methods for control of physical, printed engineering drawings in a build-print manufacturing environment?
Kyle: Yeah, this is an example that, if we’re talking about the physical drawings you need to have physical security. This question seems more focused on physical security. You must secure your building with locked doors and utilize a form of badge access and tracking in your facility. And your must restrict access in your office area to people who have been cleared through background checks.
Question: Is it or isn’t it CUI?
Scott: Got it so question number nine is from another company. They’re trying to determine if they have CUI. They believe that they’ve got emails that contain contracts, purchase orders and all that sort of information. But they don’t believe it is CUI and they haven’t seen anything come through on any paperwork that has been labeled that way. So how do they determine or validate if they have CUI? And what approach should they take for CMMC?
Kyle: This is a common issue because some documentation supplied from the government may not have the required CUI marking on it. Nor in the email it was sent in. I’m not saying those aren’t CUI because there could be CUI information that’s not marked. But let’s discuss this: Is it considered CUI even when it is not marked?
When in doubt, ask your contract officer
It’s best to get clarification from your contract officer. Go back to your customer contract officer or the customer program manager from your prime customer. And look into the CUI registry to determine if it is CUI. But coordinate this with your contract officer or your customer program manager. It’s best to be able to say whether it is or isn’t CUI based on the DoD CUI registry. I understand this can be challenging but it’s important to align everyone’s understanding and expectation.
Question: CMMC DoD for home offices?
Scott: Got it. I’m going to move to question 12. Now this is one I’m sure many people can relate to due to COVID-19 this past year. The question is: How do you handle a scenario for home office working environments since the office has got limited access?
Kyle: There is a lot of talk about this one because there’s confusion about how to secure home offices. But if we are talking about CMMC or NIST 800-171, it’s an alternate working place so you still need to apply the same security requirements in your home environment – your home office. So, create a separate network to handle your CUI information. When you work with CUI, use a separate, dedicated wireless connection that is only for you. And use a VPN (Virtual Private Network). Those are just some of the requirements of NIST 800-171 that will apply to your home office.
Question: Recommendation for tracking CMMC DoD assessment readiness?
Scott: Great! And now I’ve got question 13 from an individual that’s a CMMC project lead within their company. How do you recommend tracking progress in readiness? This firm’s done a lot of that work but tracks it using Excel. It doesn’t seem to be the most efficient tool. What would you recommend?
Kyle: Obviously there’s a solution like Exostar’s Certification Assistant. Otherwise it will be very difficult for you to track using an Excel spreadsheet. You need to track all the policies, procedures, practices, and the evidence to support these practices. Use a smarter, better tool. The Exostar Certification Assistant is among the best available tools. It can simplify management of documentation and tracking to see how well you are doing with compliance.
Exostar offers a trial version of Certification Assistant
Scott: Thanks Kyle. Exostar Certification Assistant is available for a 30-day free trial. It does everything from self-assessments and SPRS scoring to generating artifacts like your POAM’s and your SSP’s as you progress. Compliance is a journey, it’s not just at one time “build your SSP” type of exercise. So having tools like this definitely facilitates compliance tracking, especially if you’ve got multiple people engaged in a company project.
Question: CMMC flow down requirements, and is it or isn’t it COTS?
Scott: The next question is 14. How do you see CMMC DoD requirements flowing down to COTS (Commercial Off The Shelf) providers?
And how do you suggest COTS providers handle situations where prime contractors might try to force the requirements down?
Kyle: Yeah, I think we talked about this earlier. Understand the definition of COTS, then you can go back to the government to persuade them CMMC requirements don’t apply. You can search google for it, It’s FAR 12.103, it defines COTS. Make sure you understand what COTS is. And make sure you actually fit the definition. Then you can confidently talk with your contract officer or your prime contractor program manager. Tell them, here’s the definition, and this is all we do. We meet the definition of COTS. And based on CMMC requirements – we are exempt. So, you have some homework to do to show you are exempt. You are not in scope, because you are providing COTS and are a 100% COTS supplier.
Some companies sell COTS but still handle CUI
I have heard of some edge cases where COTS providers are also providing cleared services to the Federal government. In one case, a company received information marked as CUI. They handle and manage CUI even though it doesn’t come from their COTS contracts. So that’s just a cautionary tale. If you’re doing some of those other services you might be viewed through a couple of different lenses. Also, if you’re a COTS provider and you don’t need to receive this additional CUI information, ask your customer to not send it to you.
Question: CMMC DoD for air gapped networks and legacy equipment?
Scott: Very good advice Kyle. So, the next question is #15. It’s about air gapped networks. How does this fit into CMMC? And how about active servers that are too old and not being supported but are still used, how do they fit in with CMMC? I’ve heard from a lot of people where some of these old servers are still needed, still being run, any thoughts on that?
Kyle: Yeah, and this is common, especially if you are manufacturing for the aerospace industry. You probably have older CNC machines from the 1980s and 90s. They require Windows 98, Windows NT, or Windows 2000. So, there are still old systems out there that require old operating systems and those aren’t updated with security patches any longer. This makes them risky. CMMC and NIST 800-171 require segregating these outdated systems into a separate network. That minimizes the risk, in case they become compromised. If segregated, it will not impact the rest of the network. So you want to have the proper network segmentation to reduce your risk.
Question: Where to find C3PAO’s?
Scott: Great now here’s a question about C3PAO’s. How do people find out who the C3PAO’s are and when they will be available? Because I know there’s a lot of hype out there but where should they go to find out? I’m also curious?
Kyle: I would go to the CMMC-AB website. You’ll find the latest C3PAO status on their marketplace page.
Scott: Excellent and I sat in on a town hall last night held by the accreditation body. They showed a slide presentation that had some updates about the progress of C3PAO candidates in the funnel and who is going through that process. The CMMC-AB posts their town hall videos on the their website. I’m not sure when they’ll get the one from last night posted but it was about an hour-long session.
Question: How do I know if CMMC DoD applies to my business?
Question #20: How do I know if CMMC DoD applies to my organization if it’s not mentioned in our contract? They’ve received letters from their customers stating they need to be compliant. Their company supplies metals and alloys to the DoD; pipes and other things that that go into space systems and to other systems that are DoD specific.
Kyle: Yeah, and I think in my presentation I mentioned the need to begin with reviewing your contracts. If it’s not spelled out in your contracts, you want to check the CUI registry to see if some of the information you received from your prime or the DoD is listed there. That will help you determine if you are receiving CUI even if it isn’t marked.
Talk to your Prime contract officers and program managers
Talk with your contract officers and customer prime program managers. And as I mentioned in the presentation, conduct a CUI scoping exercise based on the information you receive. Information can be CUI even when it isn’t marked. So talk with your contract officer or program manager. Understand what is CUI, and develop your CUI scope and boundary. Next, perform a scoping exercise within your organization to understand what is considered FCI or CUI. And from there you can determine what CMMC maturity level you must achieve: CMMC level one or level three. You’ll need confirmation from your customer and get something in writing from them.
Scott: Got it. Now just a quick request to the folks in the audience before we go on to the last few questions: There is a poll available, if you want to go ahead and start the poll while we do the last few questions I’d appreciate it. It’s available in the links, I believe, within the screen.
Question: If I need CMMC, does my MSP need it too?
Next question for Kyle. If we’re required to be CMMC level three (this is question #31) and we use an IT managed services provider (MSP) are they required to be at level three as well?
Kyle: Yeah so this is a good question. A lot of companies use an MSP (managed service provider) or a managed security service provider (MSSP). It’s still all about following the CUI data trail. Can your MSP see or have access to your CUI? If yes, they will be in scope for your CUI at CMMC level three. If you can find a way for the MSP to manage only a certain part of your equipment or the system that doesn’t handle CUI, they will be out of scope.
Question: Is CMMC DoD needed for a small business division who handles CUI?
Scott: I’ve heard a lot of questions around that one as well.
So, the next question is, the profile of the company is, they are a large global company with several divisions. They have multiple branches per division but only a couple divisions deal with CUI. And out of those two divisions, only certain branches deal with CUI. So how do we go about this? Can we carve out the specific branches that have to deal with level three? And leave out the rest of the company in the certification process? And what about FCI? How do I go about doing this if I’ve got a large sprawling company with different needs?
Kyle: This is going to be common when you get into some of the larger, more complex companies with multiple sites and multiple branches. You need to perform the thorough CUI scoping and data life cycle exercise that I mentioned earlier. This is the vehicle that allows you to understand how your CUI flows through your organization. What does CUI touch? The people, processes and technology? What systems, devices, databases, and applications do your CUI touch? And who within your organization touches CUI? Which departments within your organization, and which roles touch CUI?
Understand which segments handle CUI and which ones don’t
This is how to gain a better understanding of your CUI and it’s scope. You will be able to classify those system and devices, people and sites, as being “in scope” for CUI. Then you can break it out between CMMC level 3 for CUI and level 1 for the rest of your company systems. Segregate what touches CUI from FCI. So, you can pursue two different certifications. This will make it much easier within a big organization.
Question: How do I know if I need to comply with CMMC DoD?
Scott: Excellent advice! Now I’ve got time for maybe two more. I’ve had several questions – this one asks about an interpretation of how to comply; it seems to vary widely. Question #45: What documentation is required to prove that we’re obligated to be in compliance? I’ve had other people ask: How do I learn more about the specific controls and the interpretation of it? Where would you point people to be able to find the source of truth for what they need to do to comply?
Kyle: Yep, so this is a good question. For Defense Industrial Base companies, or for the C3PAO’s – we are all going back to the CMMC Assessment Guide. There is one guide for CMMC level 1 and there’s another for CMMC level 3. The assessment guides clearly spell out the requirements. They get into the explanation about the background for the practices and the assessment objectives. I identified the requirement for implementing a specific practice earlier in my presentation. So, the Assessment Guides for CMMC level one and CMMC level three is where I go.
Question: CMMC for a business segment connected with an ethernet private line?
Scott: Excellent advice! Now this next one’s a little more technical – question #43, I thought it’d be a fun one to add in. They’ve got an ethernet private line between two buildings, does it need a firewall and encryption on this segment? What’s the boundary? If this is an ethernet private line, and has CUI going across it – what do I need to do?
Kyle: Yeah, I think it depends on how they are connected. Technically speaking, you are “Layer 2” if you have a wire connecting point A to point B. That is a hardware level connection. It’s probably okay, you don’t need to have a switch for Layer 2. It’s okay for you to connect one point to the other this way.
Is it one or two physical sites?
If these two sites are actually one physical site and are required to be CMMC level 3 because one site receives CUI but the other site does not, you need network tools. Or additional equipment to segment the network. Segment out the non-CUI site using a firewall or a VLAN so one doesn’t touch the other. It will depend on the scoping: What is each site doing? If both sites handle CUI they will both have the same CMMC level requirement and the connection between two sides is not a problem. But if the 2 sites have a different requirement, you’ll need to do some segmentation work.
Webinar wrap-up
Scott: Kyle, all excellent feedback! Once again hopefully everybody’s done the poll. I know we couldn’t get to all the questions today. We received some of them from procurement and contracts folks. I recommend attending the town hall webinars recorded on the CMMC-AB website. Some of the answers may come through in those town hall meetings and that’s where they update from both the DoD and the CMMC-AB perspective, so that’s a good source of truth there.
I’d like to thank everybody for their time today and Kyle, a special thank you to you! I appreciate your wisdom and guidance that you’ve been able to offer up here to folks! And again this is all about trying to help secure the defense industrial base and doing it the right way. Thanks again everyone and have a great day – thank you!
Are you ready for your CMMC Assessment by a C3PAO?
Be sure! Gain confidence with our mock C3PAO assessment.